Cybersecurity Monthly Report (February 2024)
Ex ante coordinative defense and monitoring
A total of 47,912 pieces of government agency cybersecurity coordinative defense intelligence were collected this month (a decrease of 14,666 from the previous month). Analyzing the types of identifiable threats, the top identifiable threat was information collection (29%), i.e., mainly obtaining information through attacks such as scanning, detection, and social engineering. This was followed by hacking attempts (21%), which were mainly attempts to hack unauthorized hosts; and intrusion attacks (15%), most of them involving unauthorized access to systems or acquisition of system/user privileges. The distribution of intelligence volume in the past year is as shown in Figure 1.
After further analysis of coordinative defense intelligence, it was found that hackers recently used e-mail accounts of university staff to send social engineering e-mails under the name of the Control Yuan. The e-mails contained malicious attachments sent to government agency personnel in an attempt to deceive the recipients and plant backdoor programs to steal sensitive information. The relevant information has been provided to agencies with recommendations for coordinative defense, monitoring, and protection.
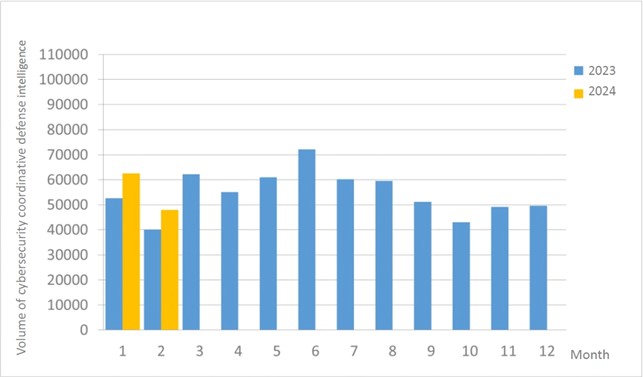
Figure 1 Statistics of cybersecurity monitoring intelligence in coordinative defense
In-process reporting and responding
The number of cybersecurity incident reports totaled 73 this month (a decrease of six cases from the previous month), with no significant difference from the number of cybersecurity incident reports in the same month last year. This month, a fire broke out in a server room of certain agency, causing external outages in the agency’s network. Some of the related agencies were also affected. The service disruption caused by the incident accounts for 62.50% of “equipment issues” this month. The statistics of cybersecurity incident reports in the past year are as shown in Figure 2.
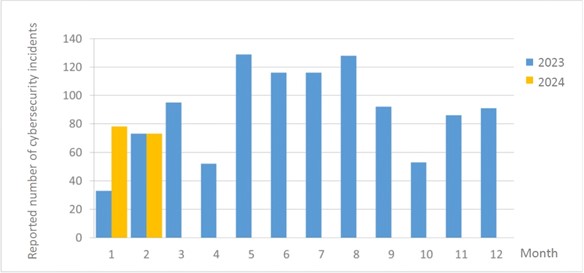
Figure 2 Number of reported cybersecurity incidents
Post information sharing
The Domain Name System (DNS) of some agencies is centralized upward. Therefore, when a fire broke out in the server room that housed the agency’s network and DNS service hosts, both internal and external network services were disrupted. The agency’s official website was unable to provide external services even after switching to a backup network. Upon investigation, it was found that the agency’s backup DNS did not support changing the DNS pointing function, and therefore, could not assign to other DNS hosts. This resulted in the website not displaying properly. The DNS backup mechanisms should be reviewed in the future to avoid similar situations.